How to Fortify Your Cloud Security Plan
Stay protected with a unified approach to visibility, resilience and real-time response

The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
You are now subscribed
Your newsletter sign-up was successful
Threat protection is a serious part of any organization’s network, storage or active workspace—especially if you’re invested in the cloud. While the basics are somewhat easy to follow or prescribe, the real-time monitoring and any aggressive corrective actions can be challenging for the individual(s) whose tasks in the organization include both IT administration and security, plus cloud-services management.
That is, it can or will become overwhelming to control without some secondary support or a built-in solution integrated by the cloud provider. Simply expecting an ISP to handle this is not a good answer.
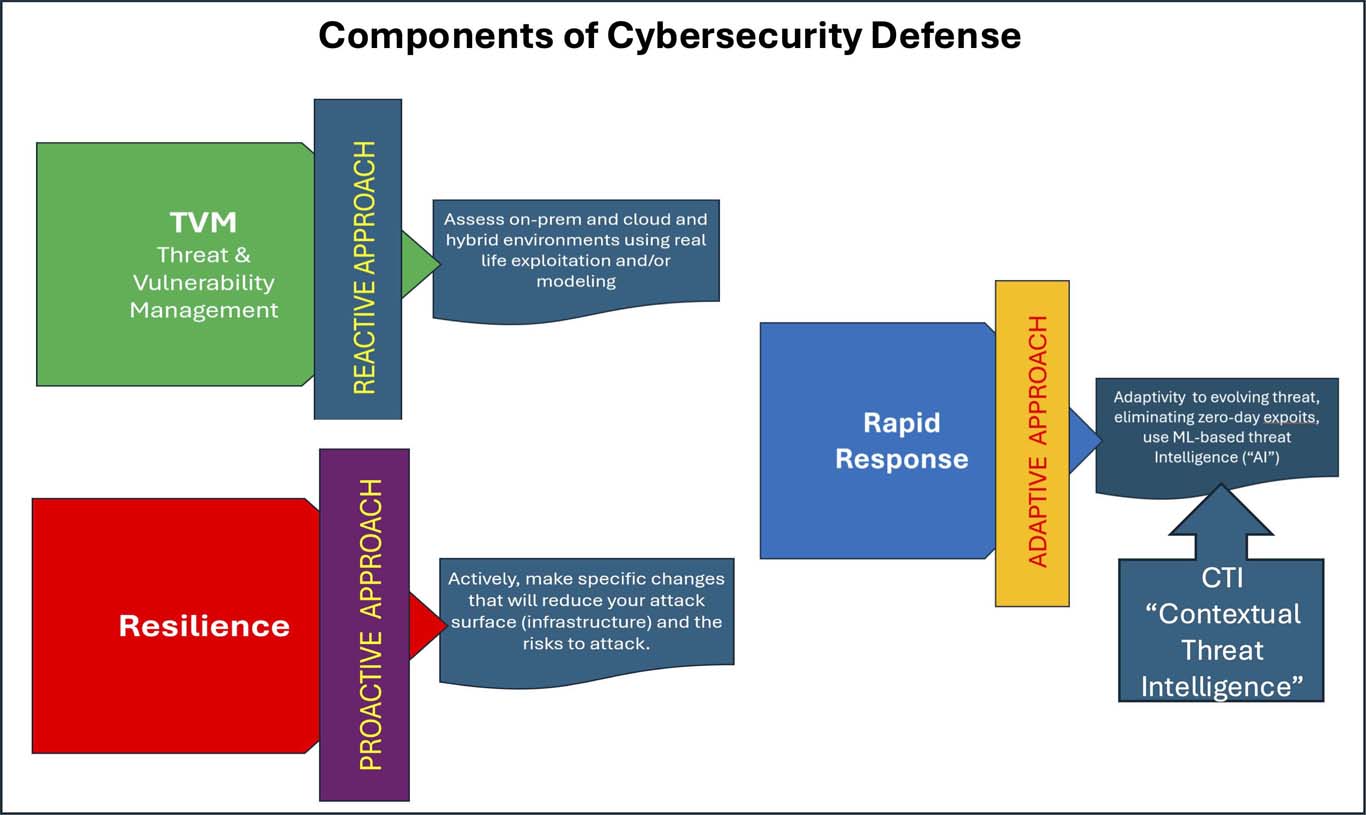
Visibility Resilience and Rapid Response
Being prepared is essential in the current cloud environment. Fig. 1 gives some of the suggestions for this preparedness from a Reactive, Proactive and Adaptive perspective.
Breaches in security can and likely will become unmanageable without appropriate planning and active, real-time monitoring alongside aggressive enforcement of IT policies and practices.
In computer programming, a runtime system or runtime environment is a subsystem that exists in the computer where a program is created, as well as in the computers where the program is intended to be run.
A cloud runtime is the environment where cloud applications and services execute—including the operating system—language support and other necessary software. Furthermore, it is a commercial term (such as Google’s Cloud Run) that ranges from a platform of managed services to the specific software stack required to run serverless functions.
Noting that, a serverless platform is a cloud-based service that automatically manages the underlying infrastructure, allowing developers to deploy and run code without provisioning, scaling or maintaining servers and otherwise is a cloud-computing execution model that allocates machine resources on an as-used basis. Examples of serverless applications include chatbots, task schedulers and Internet of Things (IoT) applications.
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
Typically, in the serverless environment, any server management, configuration, scaling and billing activities are abstracted from the end user—i.e., the complex, underlying details are hidden and simplified, so the user need only interact with a higher-level, easier-to-understand interface.
Set Up a Unified Platform
One core solution to ensure adequate security precautions is to establish a unified platform that spans across development, operations and (real-time) runtime to provide continuous visibility, protection, simple and continuous detection and proactive response.
Some of the groundwork for building a modern cloud-security program is provided in the following, as outlined by a familiar cloud-support trendsetter who specializes in providing cybersecurity in an era of change and movement toward the cloud, regardless of business model.
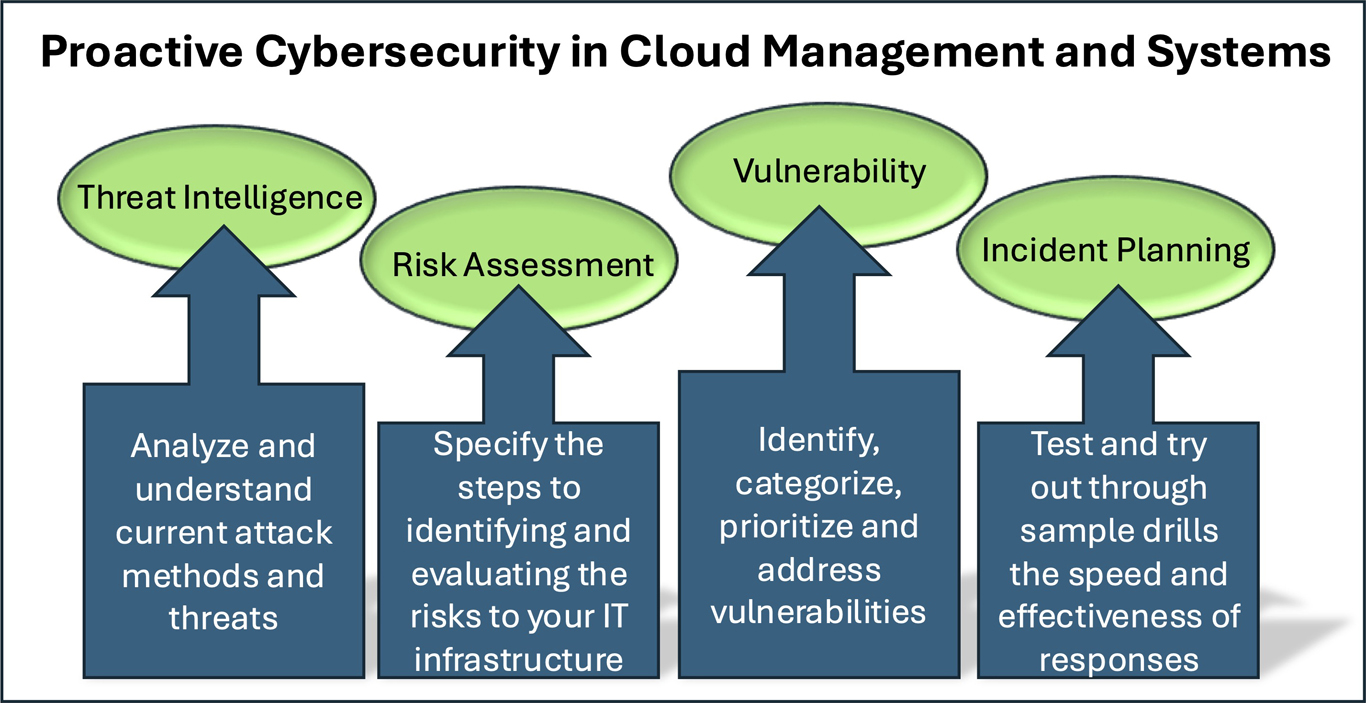
One option is to take a proactive approach to cybersecurity (Fig. 2), which is critical to reducing risks and being prepared to address or prevent breaches. Examples follow:
Container Runtime Security and Modeling
One part of understanding and preparing for cloud security involves some of the actual code-centric and application development, such as understanding Container Runtime Security, a key aspect of Kubernetes (as an open-source container orchestration platform, with cloud computing services) and security. This prospect focuses on safeguarding containers (e.g., Docker) during their execution.
When active, operational containers are most vulnerable to malicious activity since traditional security tools weren’t designed to monitor running containers. Runtime security is the only way to secure cloud-native applications at scale and in today’s environments, the use of AI and machine learning will necessitate runtime automating the processes for modeling of a healthy activity built against a model.
“Modeling” is the process of creating a representation of normal, safe behavior—for applications and services, especially when running in a cloud-native environment. Such a representation serves as a baseline to identify and detect deviations or anomalies that might indicate security threats.
When the system has an established model, and then uses continuous monitoring and lets software make comparisons of the runtime activities of applications and services against the established model, teams can then identify and respond to unauthorized actions, privilege escalations and other potential incidents. Major cloud-service providers offer managed Kubernetes services that simplify infrastructure management, allowing organizations to build and run modern applications on a hybrid or multicloud environment.
Build a Strategy for Risk Prioritization
Most security teams lack the time, experience or context to effectively handle and react to a deluge of security alerts that could come from various security tools or practices. As DevOps and engineering teams rely more on cloud technologies to achieve faster development cycle times, they may often prioritize development deadlines over security issues.
While they fundamentally understand the needs and values of security, they often don’t deem it highly important or may end up wasting their time and resources remediating vulnerabilities that seem impactful but don’t present an active risk in production. The organization’s administration should consider utilizing a tool set that correlates threat intelligence, business impact and data sensitivity to provide an accurate representation of active risk.This approach can then help in enabling alignment between DevOps and security teams as to which security issues to prioritize and when.
Avoid centralizing into one workstream that is sandwiched between DevOps, engineering (implementation/operations) and security teams. Avoid manifesting risks and mitigate the risk of a breach, since the functions of each workgroup then isolate (silo) the interdependency of each job function or task.
In the current age of cloud, one where all of your teams’ efforts are likely focused on innovation, it is crucial to leverage a solution (team, outside party or vendor) that can manage every stage of cloud detection and response for you.
To maximize the investments in a security solution, those teams (internal or external) must have the expertise to leverage activities fully. If you don’t already have those teams in place (and properly structured), then look for a solution provider that can function as a partner and who you can rely on to guard your cloud assets 24 hours a day, 365 days a year.

Karl Paulsen recently retired as a CTO and has regularly contributed to TV Tech on topics related to media, networking, workflow, cloud and systemization for the media and entertainment industry. He is a SMPTE Fellow with more than 50 years of engineering and managerial experience in commercial TV and radio broadcasting. For over 25 years he has written on featured topics in TV Tech magazine—penning the magazine’s “Storage and Media Technologies” and “Cloudspotter’s Journal” columns.