Understanding Data Protection Basics and Assessment
Data is the lifeblood of any industry that uses digital technologies for its activities

Protecting your data is a lot like your security practices. But legacy applications are no longer sufficient in this evolving digital transformation era. Some say now is the time to move on from old-school tools for data-management and look to new means for their data-protection solutions. This concept depends in part on how you and your organization view data as a valued commodity.
Storage systems and data products are a small part of the overall data-protection ecosystem. In recent times, some have claimed that so-called “legacy data-protection products” are little more than costly insurance. Up and coming new (and current) solutions can now help you address the most important aspects of data protection and help mitigate the complexity of keeping your data safe. Knowing the basics is imperative when establishing a path towards data protection.
Disruption in a New Light
The IT teams of today must look at their operations in a new light as nearly all industries—including entertainment—are being disrupted by entrants who are attracting customers away from their otherwise non-digital businesses. These new entrants can include “bandits” whose mission is to capture this data and exploit its value for themselves, including the illegal sale of that data or the ransoming of its usage by anyone, especially its owners.
The industry needs more help. It goes without saying that one of the new sets of challenges to IT-professionals includes finding sufficient workforce to support a growing set of digital requirements through the employment of its current (or newly hired) staff while continuing to protect the very assets that they manage or administer. Tools are available to aid in data protection, but it still requires proficiency and expertise in configuration and implementation of these new and usually advanced tool sets. The education and proficiency of these personnel are critical to securing the integrity of the data that they support.
Data is the lifeblood of any industry that uses digital technologies for its activities. It doesn’t matter what the business is or if it supports only a single entity or a myriad of other smaller segments within a global entity. Preserving your data is critical to survival, hence the IT industry must select from a multitude of products marketed to support and preserve this precious commodity.
Data protection is an essential function of enterprise IT management irrespective of the size or scale of the organization. As with any product you pay for, the intangible is almost untouchable until you need it, so let‘s first start by understanding what is meant by data protection.
For several years, storage solution specialists and vendors have recommended users include certain purpose-built commercial appliances in your storage architecture. Some of these legacy products were built to duplicate (clone, snapshot or other) and make available all your data sets in a quickly assessible, easily managed system that “auto-magically” would restore lost data from an independent archive platform with no losses or degradation in productivity.
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
In actuality, these appliances or solutions were found to be a non-foolproof solution for maintaining data integrity, with the need, rationale and understanding of the requirements becoming a “missing link” in the overall solution set. As will be detailed later in this article—knowing about your data and the infrastructure it works within is a great first step to data assessment and protection methodologies.
Best Practices and Assessment
One of the suggested best practice approaches to ascertaining the validity or value of your data protection program is to do a Data Protection Impact Assessment (DPIA). This practice describes a process designed to “identify risks arising out of the processing of personal data and to minimize these risks as far and as early as possible.”
DPIAs are important tools for negating risk and for demonstrating compliance with things such as General Data Protections Regulation (GDPR) especially in those areas or regions with strict adherence to data integrity and preservation where GDPR is required by law. Those companies who must comply with GDPR are likely well aware of the data-protection requirements with many guidelines and practices published widespread.
Automated processes include those principles, which are outlined in ISO 27001—the compliance document for international standard certification describing how to manage information security. ISO 27001 Certification demonstrates that your organization has invested in the people, processes and technology (e.g., tools and systems) to protect your organization’s data. ISO 27001 provides an independent, expert assessment of whether your data is sufficiently protected.
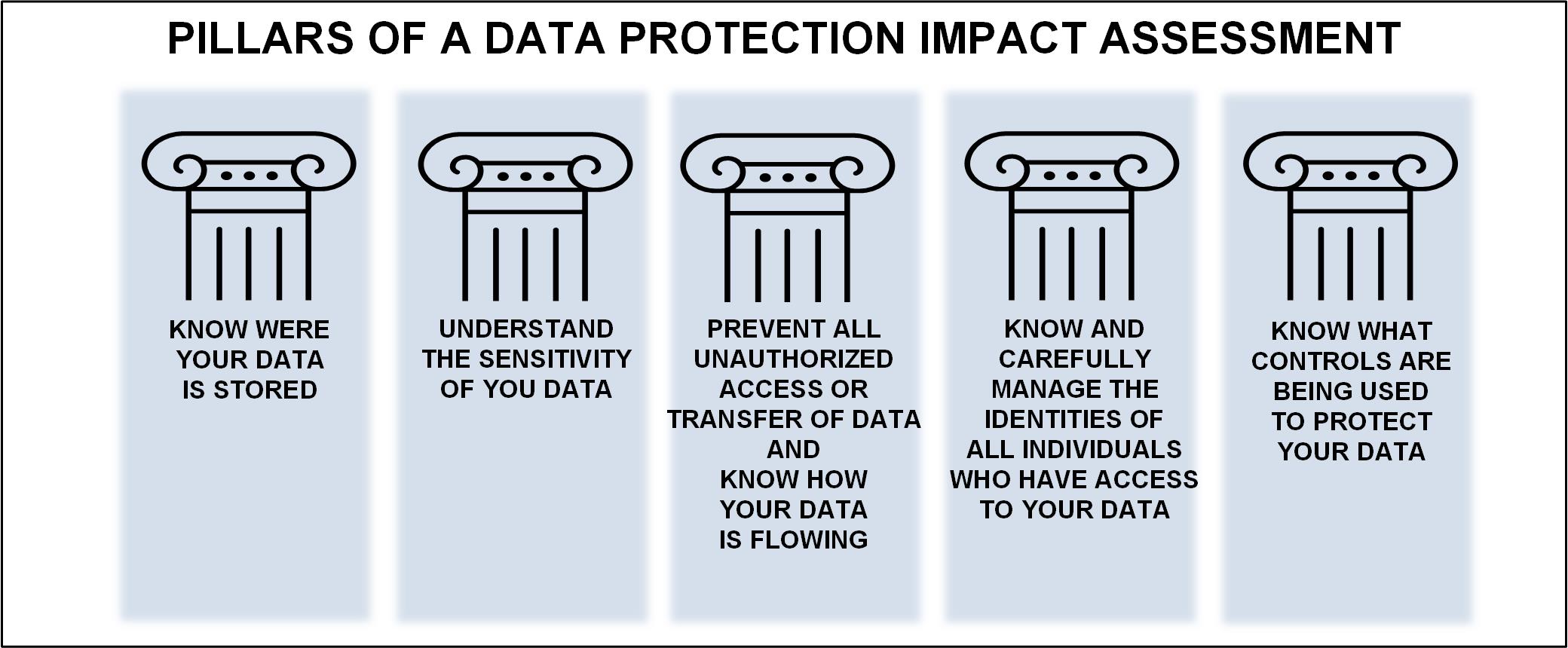
As an outline to assess if your organization is at least thinking in the right direction, the following elements are considered the “pillars of integrity” and can help you understand key issues in data-protection.
First, know where your data is stored or located, as well as how to retrieve it during compromising conditions. Second, understand the sensitivity of the data you have stored, the importance of the data to your business and the likely business impact should this data be unavailable or compromised to unauthorized parties (including the public). If the data should be modified or corrupted, know how to and what it will take to recover or restore that data.
Know How Your Data Flows
Third, owners should be knowledgeable in the prevention of unauthorized access and/or data transfer. This concept is aided best when you know and understand where, and how, data flows in your system and elsewhere (including the cloud). Unprotected environments are one of the biggest culprits to data loss and include not just the storage itself, but all those services that might have access to the data or involve interchanging that data, such as email, accounting systems, e-commerce solutions, backup and such.
Fourth, know and carefully manage the identities of all individuals who have access to the data. Determine if the right identities (both machines and persons) are permitted access and determine who should not have access to the data. Assess all third-party suppliers, partners and understand to what level they have access to the data including when, for how long, what kind of visibility they have to other sub-systems and similar security level concerns.
And finally, know what controls are being used to protect your data. Are those systems operating as designed and are they operating effectively? Are there stop gap methods that will immediately cease all access should any compromise be detected? Do you have your data backed up on premises or in the cloud or both?
The Digital Experience
Today, there are two broad ecosystems that support data management—on-premises and in the cloud. The ongoing global “digital transformation” (see sidebar for a descriptive definition) is witnessing a monumental shift from on-premises workflows to those that include and/or are migrating to the cloud. Organizations today are highly focused on the digital experience and think they have a good understanding of their customers’ digital experiences.
IT decision makers (ITDMs) see an urgent shift towards focusing on consumer’s digital experiences. Such experiences are just like security, which now requires investments in technologies, applications, people and customer access to any and all information. If you follow best practices in security and policy, likely you’ll be amplifying the integrity of your data using similar practices. l
Sidebar:
Digital Transformation by Definition
Defining the Digital Transformation (aka “DX”) is complex and broad-reaching—best identified by example with no generally agreed upon fundamental definition.
Essentially, DX involves how organizations and governments are changing their mode of operation in order to improve service delivery, be more efficient and effective in their designs, and achieve objectives such as increased transparency, interoperability and citizen satisfaction.
During the pandemic, many organizations were not ready for the digital transformation. All forms of organizations have attempted to capitalize on modern technology architectures bent on adding flexibility and agility to expand their competitive advantages amid the disruptions and experiences of the COVID-19 pandemic.
As some found out, any road to a digital transformation is seldom in a straight line. Results from expert interviews and reports indicate that “an amazing 40% of those organizations who commenced an all-out digital transformation initiative failed to achieve the desired business outcomes.”

Karl Paulsen recently retired as a CTO and has regularly contributed to TV Tech on topics related to media, networking, workflow, cloud and systemization for the media and entertainment industry. He is a SMPTE Fellow with more than 50 years of engineering and managerial experience in commercial TV and radio broadcasting. For over 25 years he has written on featured topics in TV Tech magazine—penning the magazine’s “Storage and Media Technologies” and “Cloudspotter’s Journal” columns.