Effective Content Protection for the Digitally Connected World
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
You are now subscribed
Your newsletter sign-up was successful
It is common knowledge in the broadcast industry that conditional access systems are no longer a significant barrier to the illegal redistribution of content. The HDCP portion of the HDMI standard has long since been compromised. Worse still, nothing prevents a properly licensed viewer from pointing a cellphone camera at a monitor and restreaming a watchable copy of broadcast content. The latter is in part a tribute to the quality of modern consumer cameras and displays which, properly chosen and carefully used, can create copies that look like they were made via direct digital connections.
Content producers are feeling the financial pain from rampant copying and redistribution. They are stepping up their enforcement of distribution contract provisions which demand that broadcasters protect the content that has been entrusted to them. Broadcasters in turn find that they are facing these issues with few attractive options for resolving them.
Although forensic watermarking is widely touted as the solution, many of the systems on the market are prohibitively expensive. Not only are the licenses themselves expensive but they often require wholesale replacement of all set top box (STB) hardware and the installation of costly head-end hardware.
JUST A MATTER OF TIME
Even after all that expense, the common watermarking methods are not totally robust. Most are fixed methods, often requiring hardware support, and as such are stationary targets for a hacker. Some have already been compromised. For the other content protection systems, hacking is just a matter of time.
We took the concept of watermarking back to first principles and came up with two key assumptions:
First, that presenting a moving target to the hackers is perhaps more important than the absolute difficulty of hacking any one variant of a watermark.
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
Second, that cost efficiency is extremely important right across the broadcast industry as media companies strive to deliver more channels within a finite total budget.
These factors encouraged us to research a concept in which watermark variety is the primary security mechanism. The watermark insertion in this approach is client-side rather than head-end side, avoiding the additional CDN costs of most head-end solutions.
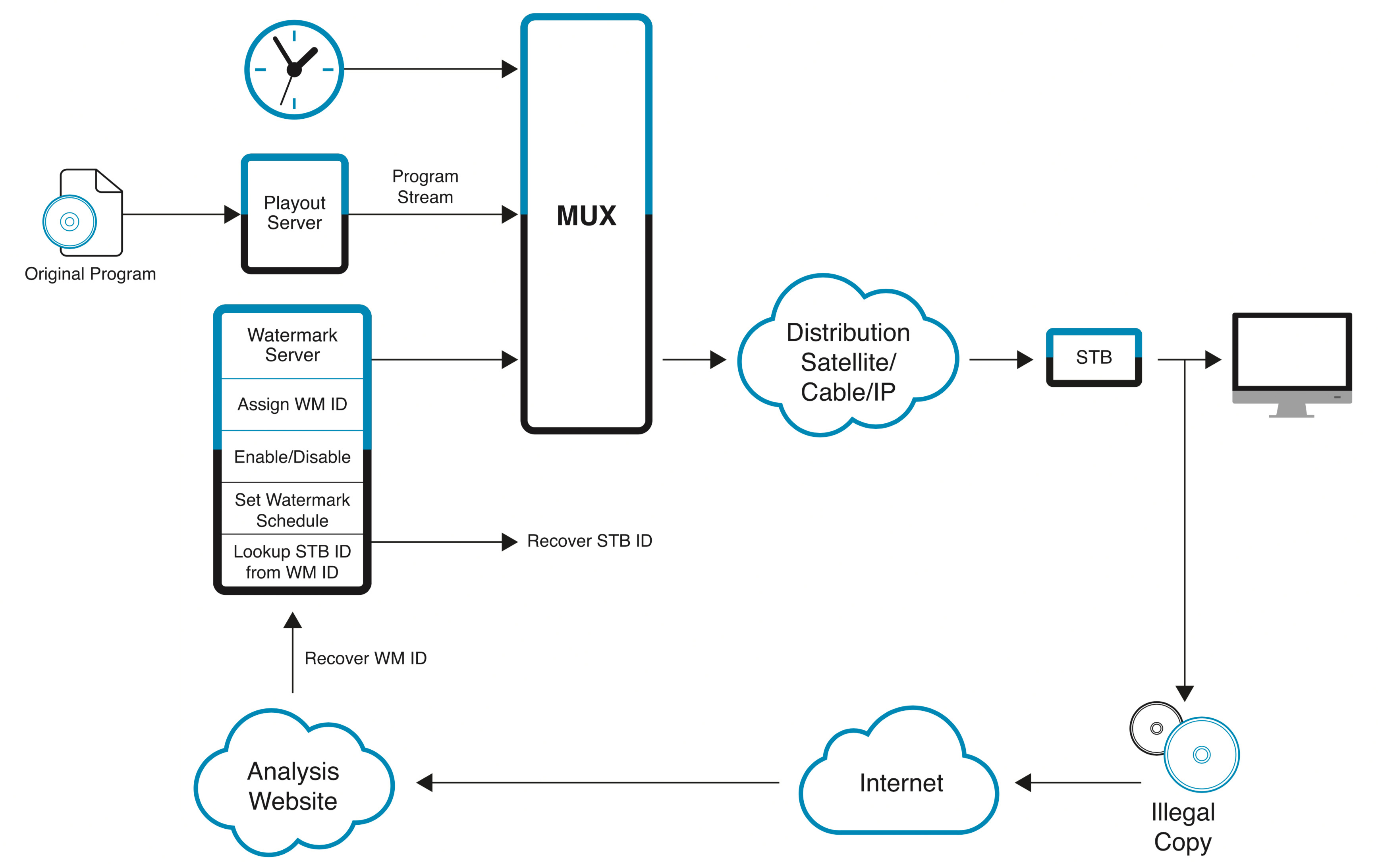
The result of this investigation was a four-element solution consisting of a watermark server with internet access, watermark set-top-boxes, a player and an analysis workstation. Watermark analysis and decoding are performed as a cloud-based supporting service which identifies any playout devices associated with illegal use of protected content. For STB based systems, this is a software-only technology that can be back-fitted to existing STBs provided that source code access to the STB is available. The components of the system are:
- A watermark control server that assigns unique watermarks to each client device and monitors their status;
- Watermark-capable STB code to insert the watermark during playout;
- A cloud-based decoder system to recover the watermarks from copies, and
- Tools to capture and forward found copies of protected content to a cloud-based decoder.
For OTT systems, there are further considerations. It was considered vital to support devices running on Microsoft Windows, Apple OS X, Google Android, and Apple iOS. Other platforms or devices could be added in the future. Because OTT devices lack the secure execution environment of STBs, the system is written to tightly bind the watermark process to the digital rights management process such that the content never exists both decrypted and un-watermarked. The code that performs this transformation is hidden by the same level of protection used for financial transaction software.
More generally, this security software to accomplish watermarking exists in two forms: integrated into a specific type of player or as a stand-alone security module usable with any player. Not all platforms support both forms. The security module can be integrated with other players if source code access is available.
For a seamless user experience, the broadcaster's servers must be made aware of the security module so that connected devices check for the stand-alone security module or the player-integrated security module and offers to download the appropriate module if it is missing.
Because of the limited processing power available in many OTT devices, a full OTT ADTH TOLKA Watermark solution requires some additional head-end equipment as compared to STB systems. The system is a combination of server-side analysis and client-side insertion. Metadata traveling with the encrypted stream tells the client side the most appropriate watermark and watermark parameters for the current content.
SUMMARY
Content protection is more important than ever in today's digitally-connected world. Content owners quite rightly expect their property to be secured as tightly as possible whenever and wherever broadcast.The technology required to achieve that security effectively and affordably is available today.
Jack Curtis, Director of New Technology, Atlanta DTH, Inc
