Exploring Internet Tunneling

Tunnels have been in the news a lot lately, such as the dramatic rescue of the miners in Chile, and the newly connected tunnel under the Swiss Alps for high-speed rail traffic.
While these are both undeniably amazing technical triumphs, they aren't the kind of tunnels that we are going to be covering in TV Technology. Instead, we are going to discuss data tunnels that are constructed through the public Internet that allow secure video and data transport.
The basic concept of a tunnel is to permit data that is formatted for one type of network transmission (say, on a corporate local area network or LAN) and actually send it over another type of network (say, over a wide area network or WAN, such as the Internet).
There are many combinations of protocols that can be used in this manner, and essentially any protocol can be tunneled through a network that supports any other. One good choice is Layer 2 Tunneling Protocol (L2TP), which is often combined with Internet Protocol Security (IPSec).
WHY TUNNEL?
The primary reason that most companies use tunneling technology is to connect between company locations and support remote users who are not able to physically connect to the corporate network. Another reason might be to provide a connection between different companies who need high-bandwidth connectivity on an occasional or long-term basis for collaboration or file transfers.
Companies sometimes also use tunneling to replace costly leased data circuits by purchasing Internet connections at both ends of the circuit, and then constructing a tunnel through the Internet. This will usually reduce the cost of connectivity, but involves tradeoffs.
One big tradeoff is security (which we will cover later)—it is much more difficult for an intruder to penetrate a private telecom circuit than it is to simply sniff packets on the open Internet.
The second tradeoff is reliability—the amount of bandwidth available through a tunnel is highly dependent on the amount of other traffic present in the network. In the Internet, users have essentially no control, and have to deal with whatever performance they happen to receive. As users of popular voice services like Skype can attest, the fact that a connection that has worked continuously for the past 10 minutes is no guarantee that it will continue working for the next 10 seconds.
BASIC TECHNOLOGY
All of today's major data transport protocols break up data into discrete blocks or packets, and then add protocol headers (and sometimes footers) to the front of each data packet. These headers are formatted according to precise rules, which allow the networking equipment (such as routers) to figure out how to send each packet along towards the appropriate destination.
While the rules for header data are very strict, the rules for the data portion of each packet are wide open—basically any data that can be represented as a series of bytes can be inserted as a data payload. This openness is what allows tunneling to work, because it permits packets that are formatted for one protocol to be inserted as data inside a packet that has its header formatted to comply with another protocol.
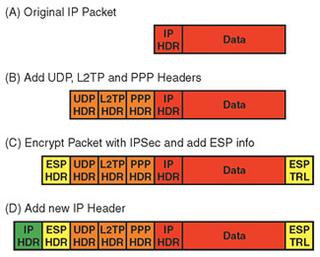
Fig. 1: Formatting a packet for tunneling To illustrate how this works, consider the example of L2TP and IPSec. In Fig. 1, the original packet is shown in red as (A). Several headers are then appended to this packet—first, a point-to-point protocol (PPP) header, then an L2TP header, and finally a user datagram protocol (UDP) header, as show in orange in (B).
These three headers, which provide the information necessary to process the original data packet properly in the receiving device, are then encrypted using IPSec. This process, called the "encapsulating security protocol" (ESP), surrounds the data that is being encoded by the encryption algorithm by adding both a header and a trailer to the packet as shown in yellow in (C). Finally, a new IP header is added as shown in green in (D), which contains the addressing information necessary to transport the data over the Internet.
Take a moment to consider what has been done here. We have taken a packet from a local network, wrapped it inside several new protocol headers, encrypted it, and prepared it for transport across a public network. The IP address on the original packet is completely hidden from the Internet, so we can extend the address domain of the corporate network without having to worry about any conflicts with other hosts outside of the tunnel environment. This scheme even allows multiple devices to share the same tunnel.
SECURITY IMPERATIVES
Why is security so important in a tunneling environment? Keep in mind that many tunnels are configured to extend a corporate network over the public Internet, so that if an intruder was able to gain access to a tunnel connection, there is no telling what kind of damage could be done.
There are many different kinds of attacks that can be made, including unauthorized user logins, hijacking of a successful connection, recording the login sequence of an authorized user and replaying it, intercepting tunnels in mid-stream and listening to the conversation in both directions, injecting extra packets into the conversation, to name a few.
Security technologies are available to address all of these potential attacks, but they must be installed and configured properly for them to be useful. An effective security system must have a way to perform each of the following functions:
User Management includes authenticating users to ensure they are who they claim to be and managing the resources they are can access. Some form of secure user password management is typically required here, with both manual and automatic systems used. Some companies also add a logging or accounting function in this category in order to allocate system usage charges among users.
Data Security and Authentication includes keeping data private from third parties and protecting data from unintentional or malicious modification. This requires some form of encryption and a secure method for distributing the encryption keys to both ends of a communication channel. This also requires a mechanism to protect the transmission path from injection of false data and from attacks perpetrated by recording previous data transmissions and replaying them with different packet payloads.
THE DARK SIDE OF TUNNELING
Of course, all the benefits of tunneling wouldn't be possible without at least some added costs. One of the major system impacts is due to the increase in overall packet size, caused by the additional headers that are required to tunnel through a network. For small packets, this extra header information can start to add up—an extra 8 bytes of data on an 80-byte packet would increase the overhead by 10 percent. For large packets, the overhead percentages are lower, but there is another danger—if the packets become too large, they can be subject to fragmentation.
Fragmentation happens to packets whenever they are too long for the network that is transporting them. For example, many Ethernet networks use a limit of 1,500 bytes for each packet (not including the Ethernet headers). If a packet exceeds this limit, it is broken into two packets and sent along to the destination, which must then be able to deal with the fragmented data.
DIGGING TUNNELS
Given the cost and flexibility benefits of tunneling, it would be surprising if the deployments of this technology didn't continue to increase. As long as the tunnels are configured carefully, with an eye toward security, they can provide perfectly usable service most of the time. However, just be careful not to expect too much from these installations—tunnels everywhere are subject to an occasional disruption or traffic jam, whether virtual or real.
Wes Simpson is an industry consultant and author of "Video Over IP, Second Edition," from Focal Press. Your comments are welcome towes.simpson@gmail.com.
Get the TV Tech Newsletter
The professional video industry's #1 source for news, trends and product and tech information. Sign up below.
Wes Simpson is President of Telecom Product Consulting, an independent consulting firm that focuses on video and telecommunications products. He has 30 years experience in the design, development and marketing of products for telecommunication applications. He is a frequent speaker at industry events such as IBC, NAB and VidTrans and is author of the book Video Over IP and a frequent contributor to TV Tech. Wes is a founding member of the Video Services Forum.

